CTB Locker ransomware or how to decrypt encrypted files
CTB Locker
CTB Locker ransomware (that sometimes goes under the name of Critoni or CBT Locker as well) was first noticed in July of 2014.This virus aims to encrypt various files and asks for a ransom in order to decrypt them. Almost all versions of Windows, including Windows XP, Windows Vista, Windows 7, and Windows 8 can be affected by this ransomware. Exclusive attribute of this malware is that it communicates with the Command and Control server over TOR. Interesting fact – everyone can purchase CTB Locker online for around $3,000 United States dollars. For that amount of money you will get the basic kit and a full support from developers of CTB Locker on how to setup everything right. This means that a lot of versions of this virus with a different appearance can be out there. The malware got changed couple times since starting, though anti-malware tools like Spyhunter, malwarebytes are capable at detecting and removing it before it installs itself.
All files encrypted by Critoni are set to CTBL format and are not available to be opened. Once installed, this ransomware will scan your computer to find out what files you have on it and then encrypt the larger part of them (not necessary all of them). What happens next is that a large window is displayed on your screen. It looks like this (see below). It will state that your personal files are encrypted and if you want them back, you will need to pay a ransom of about $120 United States dollars. Payments are done using Bitcoin payment system.
If your computer is infected with Critoni, you should be able to see a folder with a random name in the %Temp% folder on your computer. This malware will be started every time you log in to your system. CTB Locker uses elliptical curve cryptography to encrypt users’ files and that is quite a unique way to perform this. Once CTB Locker is done scanning your system and encrypting files, you will be shown a message with instructions how to pay the ransom. Furthermore, your wallpaper will be changed to the %MyDocuments%AllFilesAreLocked .bmp file, where you will find a detailed information how to pay the ransom. Other files, that will also be created and accessible for a user – %MyDocuments%DecryptAllFiles <user_id>.txt and %MyDocuments%.html. There you will find the information needed to get to the malware’s official website and complete the payment. Because intercourse with Command and Control server is executed exceptionally only through the TOR and not the Internet, it is more complicated to law enforcement to track this ransomware. However, it is not impossible. You should also know that every single time you reboot your system, CTB Locker malware will copy itself with new and random names in %Temp% so it is possible to find tons of strange-looking files out there.
Now, the first step when you realize that your computer is infected with Citroni ransomware – scan your system with a trustworthy anti-malware, such as Spyhunter or malwarebytes. The sooner – the better. It is really difficult to indicate this malicious application on your computer until the screen with the message that your files have been encrypted shows up so it would be wise to scan your computer once in a while to prevent this happening. However, if your files are already encrypted, you can still scan PC and at least remove the infection so no new files are generated every time you restart your Windows. In case you want to perform this manually, you need to remove all executables from the %Temp% folder and remove the hidden job in the Windows Task Scheduler. Notice, that this will only remove the virus and no files that are already encrypted will be decrypted. At the moment there is no known method to decrypt files encrypted by CTB Locker. There are a lot of tools developed to decrypt files encrypted by other malware, but they are not capable to decrypt files encrypted by CTB Locker. There are only two ways to retrieve your encrypted files – either pay the ransom or restore files from a backup. Open %MyDocuments%.html file to find out which files were encrypted and need to be restored.
The message by CTB locker looks like this:
Your personal files are encrypted.%f0%%c0%
Your documents, photos, databases and other important files have been encrypted with strongest encryption and unique key, generated for this computer.
Private decryption key is stored on a secret Internet server and nobody can decrypt your files until you pay and obtain the private key.
If you see the main locker window, follow the instructions on the locker. Overwise, it’s seems that you or your antivirus deleted the locker program. Now you have the last chance to decrypt your files.
1. Type the address %c1%http://torproject.org%c0% in your Internet browser. It opens the Tor site.
2. Press ‘Download Tor’, then press ‘DOWNLOAD Tor Browser Bundle’, install and run it.
3. Now you have Tor Browser. In the Tor Browser open the %c1%http://%onion%/%c0%.
Note that this server is available via Tor Browser only.
Retry in 1 hour if the site is not reachable.
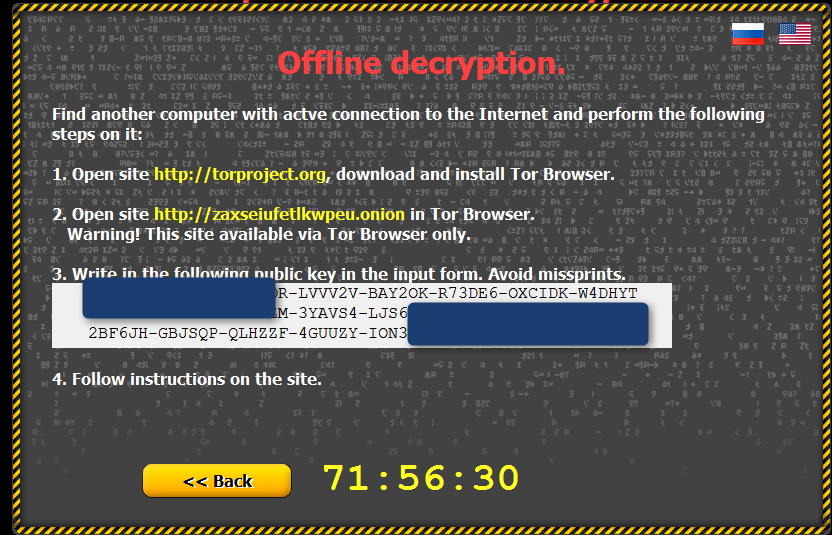
4. Write in the following public key in the input form on server. Avoid misprints.
%f1%%c1%%key%%f0%%c0%
5. Follow the instructions on the server.
These instructions are also saved to file named DecryptAllFiles.txt in Documents folder. You can open it and use copy-paste for the address and the key.
How to decrypt encrypted files
As we have mentioned before, there is no possibility to decrypt files that have been decrypted by CTB Locker. If you are not going to pay the ransom for the cyber criminals, you can restore your files from a backup. There are several ways to accomplish that.
The best option is to simply restore all system settings and settings from a Windows backup. However, it is possible only if you set up a backup before. If you didn’t performed this before, you will not be able to do a system restore. Even if you have a valid restore file, it might be not possible to retrieve lost files, if the directory they are stored in is not covered by Windows backup (you can choose that in settings).
The following method can be quite effective as well. CTB locker does not just encrypt the file – it makes a copy of it, encrypts it and then deletes the original file. For this reason, you can use particular software to restore lost files. For example, R-Studio or Photorec could perform this task. If you are wondering why it’s not recommended to wait long after CTB locker gets on your system, it’s because the longer you wait, the harder it will be to file restore programs to retrieve your deleted and un-encrypted files.
Shadow Volume Copies
In case you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. CTB Locker usually tries to delete all possible Shadow Volume Copies, but sometimes it fails to accomplish this. It is worth mentioning that Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer.
Native Windows Previous Versions
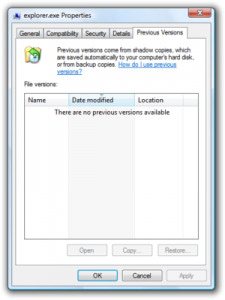
Just right-click on an encrypted file and select Properties>Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Just choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
Shadow Explorer
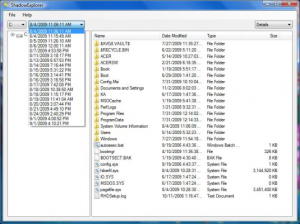
It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program and on the left top corner select the drive where there is a stored the file you are looking for. Next you will be shown all folders on that drive. To retrieve a whole folder, right-click on it and select the option “Export” and choose where you want it to be stored. That’s it.
How to restore files that have been encrypted on DropBox
If you used to store your files on a DropBox (most common, web-based file storing service) and they have been encrypted as well, you can use a few tips listed below.
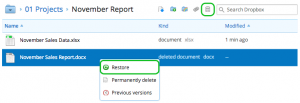
To retrieve encrypted files on a DropBox, simply login to your account on the DropBox website. Then navigate to the folder where there is the file that you want to retrieve stored. Right-click on the file and select a Previous versions option. Now you will see all available previous options of a given file (like in Shadow Volume Copies). Select the desired version and click Restore button.
just got hit by this nasty ctb-locker virus. it has encrypted pretty much everything on my computer. I tried the shadow explorer software, and even though I have windows 7 home premium and, by default, restore points is supposed to be ‘on’, in my case it is not. Panda decrypt didn’t work either.
I am wondering if anything is available yet to decrypt the affected files.
thank you for any help.
Tony
There are no known free decrypter as for know
just got hit by this nasty ctb-locker virus. it has encrypted pretty much everything on my computer. I tried the shadow explorer software, and even though I have windows XP , by default, restore points is supposed to be ‘on’, in my case it is not. No software decrypt work either.
I am wondering if anything is available yet to decrypt the affected files.
thank you for any help.
Aloke
We are sorry, but there is nothing you can do to decrypt your files as for now. If we discover the solution we will definitely notify you.
Please notify me too if you have have a solution to decrypt my encryted files. I was infected with the CTB locker. My IT cleaned my computer from it but my files on the computer are still encripted.
Many thanks,
Krisztina
We sure will do, Krisztina
hi
kindly email me on my email id: syednomanhusain@hotmail.com
i will show you…how to restore file…if you did not make any change into your computer
Will surely do Krisztina
Please notify me too. I was hit by CTB Locker, so many family photos lost.
Many thanks,
-Bill
You could share instructions right here, in the comments section.
As a last chance I opened the http://w7yue5dc5amppggs.onion/ page with Tor Browser as I was instructed in the message received with the CTB locker and here got the option to decrypt 1 encryted file before I pay 2,5 Bitcoins, I guess to convince me that decrypt is working. So I have uploaded 1 file with the extension “ingoauj’ (all my infected files have this extension) but I received the message that this file do not contain the public key which was sent in the message received with the CTB locker.
Is this possible? Why they do not recognise their own public key anymore?
Did someone try this path?
Sometimes viruses malfuntion. If they can’t decrypt single file, the key is wrong and they won’t be able to decrypt others too.
Hi Krisztina,
Beware when you pay ransom. Are you sure doing so would enable you to get the right key and it would de encrypt the file?
I received one mail froom a gentleman called Syed who asked me to send him a mail and he shall help me de encrypt the files.
I have sent him a mail but haven’t yet heard from him. He told he can help provided the file is Original. How true I have to yet see
to believe. This is FYI only.
Hi Krisztina,
My affected files had different extension nbrxlyz. CTB locker message said to pay within 7 days or else the key to de encrypt will be lost. Is your time frame beyond seven days? Check.
Hi All.
Below message posted by a gentleman claiming he can help de encrypt files. Authentication is not guaranteed so check before you decide to write to him. I don’t stand guarantee/authentication of the genuineness of his claim.
Quote :
hi
kindly email me on my email id: syednomanhusain@hotmail.com
i will show you…how to restore file…if you did not make any change into your computer
Hi,
I just read everywhere that there is a time frame but I have none.
So before any payment I had the option on this page to decrypt one single file from my computer that they can demonstrate that they have key for it. So I have uploded one file but they could not decrypt it. The message from the derver says that the file did not contain the public key or was encrypted on another computer. So I did not pay because they could not demonstrate that they have the private key to my files. I was informed that this could be viruses malfunction.
They just distroy others work and computer but work with mistakes do not brings money.
Thanks for your advise, I will contact this gentleman and try all possibilites to get my files back – photos and videos from my children making the first steps (the precious of all).
Its frustrating , all my hard work of two years without any back up is encrypted .I did not find any support on net for retreival .If someone could able to extend help please do so.
Thanks in advance.
K.P.Kumar
please could you also inform me if you do find a solution. i am not willing to pay the “ransom” as i have no quarantee that i would get the right key to unencrypt my files. i work from hom thus all my client’s information, application and so forth have been encrypted. this is not a goo start to 2015. i would appreciate if someone could let me know as soon as they do find a solution to this madness. thanks
please everybody if you got any information about decrypt the files please send me.
Hi, If I could also be informed once there is a way to decrypt. All my files .ASBUMDH, so frustrating.
Thx
Hi Cules,
As of now no resolution found. I shall keep you posted if a solution comes at hand. Please do let me know in case you get one.
All the best to move on keeping this behind you , hopefully as I know it is tough.
Hi Syed,
I sent you two files by email. Any progress which can make many people around globe feel relieved from this menace?
Hi ,
my all important 5 years data got encrypted with a extension GTUKOEA. can any one help me to decrypt it .kindly mail me to vishwasba@gmail.com
regards
my all files extension is > .gtukoea . I renamed it to .doc . No use. Spent oneday in downloading all recovery softwares. No use . Please help me
Been hit with this as well, all I can say is sick as… years of coding work, family photographs all down the pan.
As far as my understanding of encryption goes unless you have the required key (on their servers) you’ll be hard pushed to undo what’s been done.
I’ve wiped and reinstalled the raid setup I had and disconnected the drives with the infected (or encrypted files) I have left in the hope that someone eventually finds a solution, I’m just doubtful anyone at this point can.
If they ever catch the people / person that’s done this… prison time and lots of it.
Please Syed help me in this case
THANKS FOR HELPING TO ALL
Please inform me to thank you
Hi all, I have a client who’s been hit with the same virus. it also names all the files with file extension ‘Gnoorën”
I could not even run backup so all I did copied all files to external Hard drive, reinstalled windows 7 but still the backup files are still corrupt.
Any help on how to solve this problem will be highly appreciated.
Hi Keith,
As of now, no relief in sight. As soon as one comes to me I will share with all and request everyone to do the same thankfully.
Hi aloke,
As I posted here long back about my all files encrypted and changed to the extension “GLUKTOE” ,, I searched all websites and ran several programme to decrypt my files. But so far not succeeded to recover my files. Unluckily I did not take windows back up and I don’t have any server to restore a shadow copies of my data. Most of the single user will not be taking any windows back-up.
What I found is my registry also got edited and I could see that “GLUKOTE” extension values. I am afraid to modify any registry setting . I feel if any one could work one registry ,we all victims could get a solution to encrypted files.
Regards
Hi Viswas,
I am aware. My files have been sent to many software engineers and they are working on it but till date no relief.
As of now its advisable to keep the files parked on a Hard Disk and move on and wait for that day when someone
comes out with the solution.
Its tough to resign but life has to move on and hope has to stay.
best wishes
Aloke
my computer is infected – no ransom paid – my files are backed up on an external drive. The virus has not been seen on the external drive. I wish to wipe all files and reinstall windows 7 with an antivirus set up on the infected computer. Will this remove all the virus? any tips appreciated.
Yes
Hi! I have got CTB locker and was so afraid, because I preinstall computer, but many files are with type: IYHFSK Could I change it? Please help!
I never seen a forum of discussion where people don’t understand the problem
1. If you data are Very important …go and pay the ransom of 700 dollars . …or wait until FBI or police catches their server and offers decryption for free
2. people who claim that they have this FIX..they LIE. PERIOD. There is no fix without obtaining private key
3. The only way to restore is with VOLUME SHADOW COPY . Find a program named Shadow Explorer and try to restore the state before infection
Hi Agron,
What new have you brought to the Forum having commented in your opening remark No one understands the problem…
I am sure every affected Individual on this Forum is aware of the problem they are into and have resigned to the idea that decrypt is not possible without Ransom but are strongly against the idea of paying the ransom.
All we keep discussing and posting on this forum is our views, problems and request to know from our fellow ship if there has been a solution that one has come up with or known to share. Its as simple as that.
I think your opening comment ” I never seen a forum of discussion where people don’t understand the problem” is uncalled for as everyone on this Forum are aware of the problem..
Thanq
I said ” I preinstall computer” The Shadow explorer does not shadow copy! I apologize for my ignorance, but I think the forum is a different problem solving and answers
Dear Good People,
I know that It sucks to have all been victims of these life-less “net wastoids”,( whom, if not for themselves being “encrypted” with anger, negativity and overall BOREDOM) could actually be of positive use to the Tech. World,( yet spend their time creating ways to ruin good peoples lives) I assure you ALL. There are TEAMS of “Comp. Nerds” (such as myself), working around the clock, for a solution to this “disgusting abuse”. Justice is coming!!! ANY LOCK can be unlocked with the right combination!
Back up your files, hold on to your information on external….and be patient.
Thank you for the assurance Brian. We pray that all you computer “NERDS” are successful and relieve us from this menace
are successful and relieve us from this menace
and help us restore our files and get back to normal life which seems otherwise so difficult. GOD BLESS ALL U GOOD SOULS!!
Please inform me to, thank you!
Hi Angela,
All my efforts to recover my Dats through the top IT professionals in India has failed.
I too am desperate to resolve the Issue and promise to all affected on this thread to share as and when I get some success and request all to share
on thread any recovery process they achieve.
Thank you for your efforts. I hope soon to find a solution.
Desperate to get 10 years of kids photos back!
I have a PST file that needs to be decrypted. Can anyone help me ?
IF ANY ONE HELP ME FOR C T B VIRUS,I LOST MY ACCOUNTING DATA
HI ALOK,
my pc has also infected by ctb locker virus and the r demanding $350 for decryption of whole data is there any procedure through which i can recover my pc data thanks and if you have found any solution please tell me thanks
If you have previous restore points saved on your hard drive, you can perform a system restore. Take a look here: http://www.2-viruses.com/how-to-do-a-system-restore
Hi Mohtashim,
Keep your hard disk aside, move on with a new hard disk installed in your computer. if you have a back up (old or recent) start working from there trying to rebuild as much as you can. Hurt you would feel but you cant sit and crib and cry.
whether you shud pay USD 350 and get the key and if or not it works is a matter of debate for anybody. For, some claims it worked some disputes as it was ransome money but didnt work. so its your choice.
all i can say is dat currently no solution to this problem is in sight.
sorry but best of wishes
Aloke
hi malik,
impossible to lose accounting datas. get ur system rechecked by your sys admin. ctb does not affect accounting datas unless dey r jpeg, pdf,xcel,word files
Please inform me too. My pc infected with last version of CTB-Locker and I have “.rsgjkpj” extension.
I am reinstalled Windows (Win 7) and copied the encrypted files for the case to appear available solution for this.
Thank you!
Hi,
my PC has been infected 2 days ago and now I have 5 GB material encrypted (family pictures, documents of all kind even text and archives)
My extension is .ojewwbm
I have the email with the ZIP file > CAB file > “papeterie_nota_bene_stationery.SCR” file
That’s the attachment which has been open so incautiously (damn!) I assume it is the downloader for the CTB Locker self.
Then I identified the file nkjmmcf.EXE which is the Program who was running in my Temp folder… I assume this one locked the files.
See Virustotal scansion:
for SCR File: SHA256 fa613da5921796bc114485420dc3449fc1ab4a4aea0b3cc5747d13d8a9020502
For EXE File: SHA256 8e6e3c99f04e72cc859dee6c01ea53b6cfcb7d9a9da0728adaefa4f990b1b967
The request is 3 Bitcoins which I WILL NEVER PAY to those bast*rds.
I had the possibility to decode “to test” only 2 files max 1 MB.
I decoded 1 DOC and 1 JPG.
Then I have now:
* the infected files
* the encrypted and decrypted files
* other encrypted and the related original files
I guess I have enough material to allow an expert to start his work and create a decoding program.
I noticed that there are several programs which decodes ransomware Trojan and old kind of CTB Locker, just no one works with this “new kind” CTB- Locker (the misfortune in the bad luck!).
Even the Tool of Panda, which allows even to create a “key” by comparing files (original / encrypted), did not give the desired result.
Maybe in 3 or 6 months someone thanks my material could create a program to decode the encrypted stuffs… and I could have my files back…
I do not know what to do, and especially do not know who contact and who to give the material.
Please help.
Please leave a reply here if you think my files could help, I will get a notification directly to my Email.
Good luck everybody and to me to!
Maurizio
any further insight to this fiasco? I had a user log into my terminal server clicked a link in his email and set this darn thing in motion. Now it’s encrypted his profile on the server, a few other files, and ANY file on the network file shares he had access to with the .ezz file extension and put a notepad document in the startup folder of all users with the instructions to be scammed. As soon as I saw what was going on, I disabled his AD account so no further infection could take place.
Short of restoring a bunch of files from backup on the network file share with previous versions and people losing everything they’ve done to those files since this infection began at 10AM this morning (it’s now almost 6PM) is there a solution to fixing this?
Infected as well…cannot believe it…and Im a friggin IT guy…unfrigginbelievable….no restore points..I think it turned off my system restore..so no shadow copy or previous version available either…wtf!!!
I’m in IT as well and got hit by this. I have no idea where it came from… I surf responsibly and don’t click on links or open attachments, etc. Lost 2 yrs worth of files.. mostly pictures. Fortunately, work related files I have backed up in a few locations, so I wasn’t totally screwed.
I hope they figure out who is behind this…..
There is nobody on the entire internet that has successfully unlock any file or photo so don’t hoop on recovery there is non.
Sorry !!
please everybody if you got any information about decrypt the files encrypted from CTB locker…Thank YOU
Great article, thanks a lot!
Can my backup get encrypted as well??
Thank you, helped a lot