Ahihi, also known as BangLuongThang02 ransomware, is a recent cyber threat developed to lock personal victims’ files with difficult algorithms and ask for a payment in exchange for the decryptor. The only way hackers behind this malware can make their revenue is from the collected ransom, therefore the features of Ahihi cryptovirus are specifically designed to scare and push compromised users to send cryptocurrency immediately without much thinking, but that is one big mistake.
Ahihi Ransomware quicklinks
- Characteristics of Ahihi ransomware
- How does BangLuongThang02 virus spread
- How to delete Ahihi ransomware and restore files
- Automatic Malware removal tools
- How to recover Ahihi ransomware encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover Ahihi ransomware encrypted files
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
So far it is known that Ahihi ransomware, which is based on Hidden Tear, has been active since the first week of January 2019, targeting English speaking users, but only yesterday the public attention was first brought to it on Twitter by @Malwrhunterteam. Ransomware experts noticed that this cryptovirus was written based on the open-source Hidden Tear project, yet demonstrated some unique and unusual qualities in its behavior. Fortunately, these features are not that notorious and 2-viruses.com team managed to find ways how to remove the threat and potentially restore the files.
Characteristics of Ahihi ransomware
Those who are familiar with ransomware type of computer infections already know that the main goal of this malicious program is to fill its creators’ BTC or any Other cryptocurrency wallet with ransom money. In order to get these virtual coins, the virus has to first get hostages worth paying for, and it does that by locking victim’s personal files with ciphers, that can be decrypted with a specific key, that is known only by the hacker, who send the virus in the first place. Although this behavior is the same for all crypto viruses, certain external and internal qualities are unique for each ransomware.
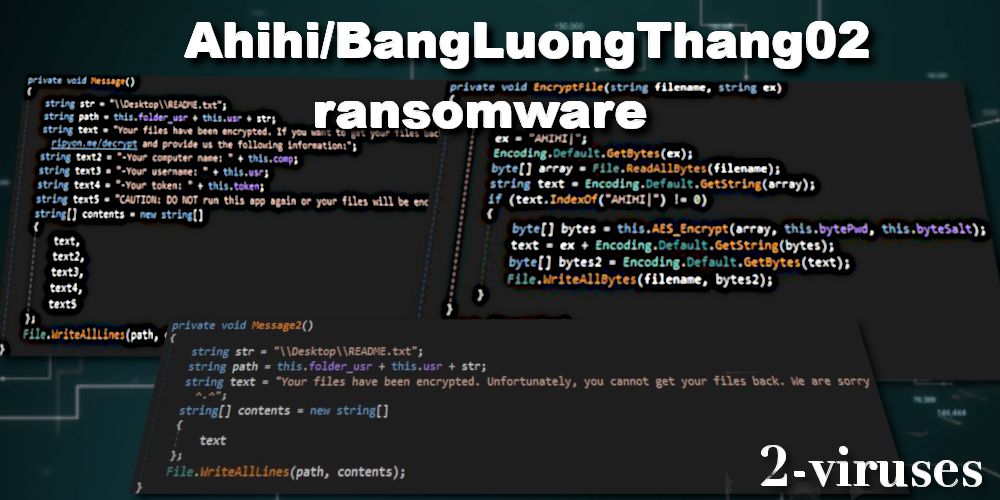
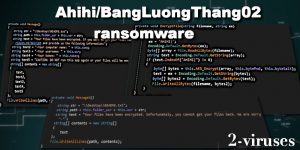
BangLuongThang02 or Ahihi ransomware is made out of an altered sample of Hidden Tear virus, which has been shared years ago for public access. This means that it uses a Symmetric AES algorithm to lock the data, however, does not add an extension to the end of affected files. But the victim knows what happened to their Windows and why all the video, audio, and other stored data is inaccessible because Ahihi virus drops a ransom note called ‘README.txt’ on the desktop with an explanation:
Your files have been encrypted. If you want to get your files back, please visit http://ripyon.me/decrypt and provide us the following information
Your computer name:
Your username:
Your token:
CAUTION: DO NOT run this app again or your files will be encrypted permanently
Malware experts noticed that if BangLuongThang02 virus cannot connect to the C2 after done with encryption, it shows another message:
Your files have been encrypted. Unfortunately, you cannot get your files back. We are sorry
The ability to perform such manipulations with victim’s Windows require a lot of fast and precise work. When the main installation file BangLuongThang02.exe is executed, it begins running background processes and altering System files and registry to ensure the persistence and that the antivirus will not detect it. At the same time ransomware looks for targeted files that potentially can be encrypted and exchanged for a ransom. This whole compromising process takes very little time, so even if you realize that you’ve installed the virus, there is no way you can stop the process. For more technical details, check VirusTotal.com analysis. It is yet unknown how much Ahihi ransomware is asking for a ransom, but the Average is around $1000, and that is because victims kept paying hackers, which we do not recommend.
How does BangLuongThang02 virus spread
Ransomware like BangLuongThang02 cryptovirus have the ability to spread in many ways (e.g. drive-by-download, fake updates, torrents, botnets, vulnerable remote desktop protocol and etc.), yet that mainly depends on the technical skills and resources of developers. Judging from the fact that Ahihi virus is based on the Hidden Tear project sample, which is available to everyone, hackers behind it are fairly new to the malware world, therefore, potentially they stuck to more simple threat distribution techniques, such as Malspam with the infected attachments. However, overall, spreading via socially engineered spam emails has been one of the Most popular ransomware distribution vectors these recent years.
Crooks of BangLuongThang02 ransomware Make up phishing email messages that pretend to be either from some client, worker, employer, bank, lawyer and etc. and state something very short, intriguing or scary but obscure, with the requirement to open the added .docx or .pdf format file for all the details. For example, the email can say that something happened to your personal data in a healthcare facility and you need to check if everything in the World file matches your information, or it can say that you have some legal issues or being sued by someone for the reason that is mentioned in the attachment. Typically, these emails can be noticed from strange, unofficial senders, grammar mistakes, unspecified recipient and etc. Once the victim opens that malicious file and enables Macros, it initiates Ahihi virus installation.
How to delete Ahihi ransomware and restore files
Throughout the years, 2-viruses.com team has dealt with plenty of crypto viruses, such as Boom, Vulston, Bizer, and came to the conclusion that the best way to remove ransomware and recover data is simply by restoring the system from the Backups to the point right before a threat, like Ahihi virus, who got in unexpectedly. Yet this technique, that we also explained in detailed steps below, is only available for those who did back up all the necessary files. On the other hand, these victims who are not so responsible and have not made any effort to save their data beforehand, can try another but still very efficient recovery solution.
Firstly, you will need to get either Spyhunter anti-spyware program and run a full system scan with it. Once Ahihi virus is found, you should proceed with given directions in order to remove it. You can use any security tool for this task, just make sure it is not a rogue antispyware and actually works before trying to restore files. For that, you can check our Reviews page where our researchers rated malware removal programs according to their efficiency.
Unfortunately, even when BangLuongThang02 ransomware is removed from the infected computer, the encrypted data still stays locked. Right now there is no official decrypting tool for this Ahihi cryptovirus, yet you might want to try the possible recovery options mentioned below in the manual removal guidelines, such as restoring from Shadow copies or using a special file restore program. If these tips did not help, the best idea would be to just keep the affected data stored on your PC, until cybersecurity specialist will come up with the Decryptor.
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover Ahihi ransomware encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before BangLuongThang02 virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of Ahihi ransomware
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to BangLuongThang02 virus. You can check other tools here.Step 3. Restore Ahihi ransomware affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually BangLuongThang02 virus tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover Ahihi ransomware encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.








