Hets ransomware is a new file-locker. It is distributed on torrent sites and is used by cyber-extortionists to collect ransom money from Hets’ victims. To make matters worse, it also installs a password-stealer. Remove the malware and change your passwords to limit the damage. As for fixing the files locked by Hets, there are some ways to restore some of that data without contacting the criminals, but those ways are not nearly as effective and certain as file backups are.
Hets Ransomware quicklinks
- How Hets works
- How to fix Hets files
- How to remove Hets ransomware
- Important -- edit the hosts file to unblock security websites
- Find and edit the hosts file
- Download and run the antivirus program
- Automatic Malware removal tools
- How to recover Hets Ransomware encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover Hets Ransomware encrypted files

(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How Hets works
Hets ransomware is a type of Djvu. This family of malware has infected thousands and thousands of people, possibly becoming the most popular ransomware in the world. Hets is just one new edition that emerged at the very end of November 2019. Djvu ransomware has had the attention of some very respected ransomware experts who have developed a decrypter free for all the victims to use. Unfortunately, the cyber-extortionists who are responsible for Hets’ development haven’t been sitting on their hands and fixed a flaw that was being exploited by Emsisoft’s experts a few months ago. This means that Hets ransomware is harder to recover from as the old type of Djvu.
Hets is ransomware that needs to be removed before the files can be recovered:
| Hets |
|
|---|---|
| How Hets locks the files |
|
| How to remove Hets ransomware |
|
| How to recover the files |
|
Hets ransomware is distributed as cracks and activated software. This is in contrast to other file-lockers that spread through RDP, infected emails and malicious ads. Hets is just uploaded on various websites for everyone to download believing that it’s a crack or program they want. This sort of distribution allows Hets to reach victims all over the world and threatens individual PC users. Generally, ransomware is targeted at businesses that can afford to pay really big ransoms, but Djvu and Hets’ makers focus on infecting individual people.
After you download run a file infected with Hets, it infects your computer. A few minutes later, Hets shows a fake Windows Update window and starts encrypting your files. As the encryption uses system resources, the update dialog is only there to throw off suspicion. Encryption makes the files to be totally unusable, as if they were corrupted. Hets marks those encrypted files with a “.hets” file extension, removing which is unlikely to have any results. You might be able to still play some of your music, get a few files out of archives, and play certain types of video with only losing a few seconds of footage. However, the majority of files that Hets encrypts are completely broken.
How to fix Hets files
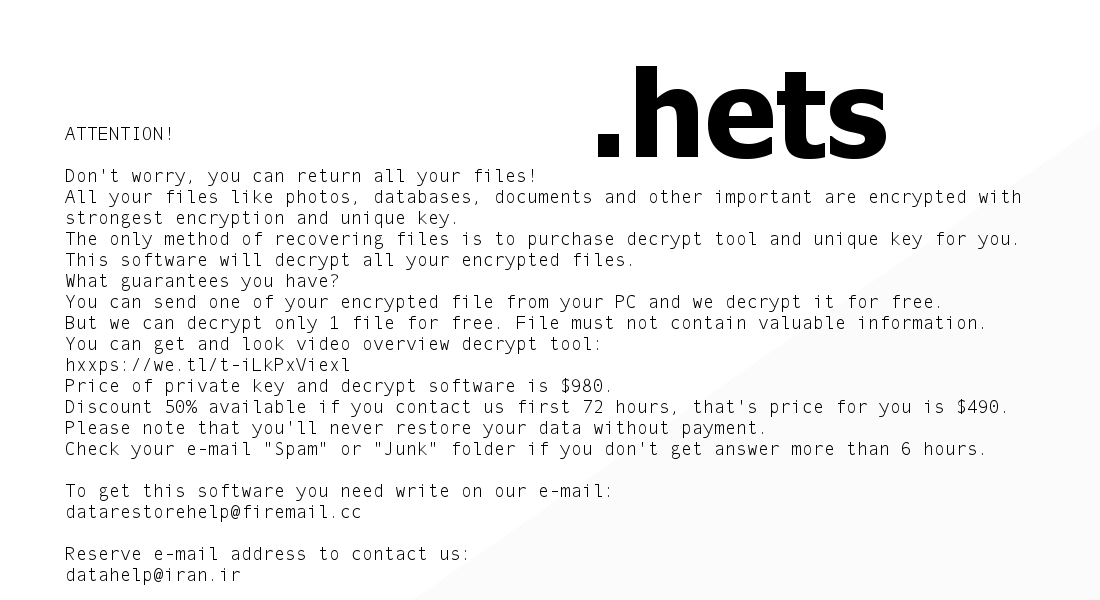
Hets leaves behind not just a bunch of files broken and with a second extension, but also “_readme.txt” files with a ransom note demanding $490 for the decryption key. Datarestorehelp@firemail.cc and datahelp@iran.ir are given as the email addresses to contact the cybercriminals on, which are common with a few other Djvu ransomware infections, like Zobm and Msop. Whether you contact the criminals is up to you, but know that it is legitimately dangerous. If you reveal too much information, they could abuse that. If you pay for your Hets decryption key, the criminals might ask for more money or they might fail to send you the correct key.
The only way to fix the “.hets” files is to decrypt them using the correct decrypter with the correct decryption key. And as only the criminals have every victim’s unique decryption key, a Hets infection can leave you feeling pretty hopeless. There is offline encryption (indicated by your user ID generated by Hets and listed in _readme.txt files and in C:\SystemID\PersonalID.txt ending with “t1”) that can be reversed by the offline decryption key, which happens to be the same for all users. But getting it would require someone whose files were locked by the offline key to pay the ransom to Hets’ operators, then to contact someone in charge of the Djvu decrypter and give them the key, who could then share it with everyone. The offline key is the only such key that is shared among all Hets victims because it’s hardcoded in the Hets ransomware. If the ransomware doesn’t need to resort to using it, an online key is generated and can only be recovered from the criminals.
Some other methods for recovering your files are listed in the last section of this post. But keep your expectations low. Hets deletes shadow volume copies and restore points, and though they’re always worth trying, the chances of success are low.
Before decrypting Hets files, take the encrypted files and make copies. If you ever get to unlocking them, whether with Emsisoft’s tool or especially if you pay the ransom to the criminals (which is a bad idea), always have backup copies of the “.hets” files. If you use the wrong decryption key, the files might get corrupted even further, which is why backups are useful.
How to remove Hets ransomware
First of all, Hets might have messed with your settings to block some cybersecurity blogs, like ours. You can fix that by fixing your hosts file, after which you can download any competent anti-malware tool (for example, ) and use it to get rid of Hets, Azorult, and whatever download was responsible for infecting you.
For now on:
- Be more careful where you download files from.
- Scan downloads with a strong anti-malware program.
- Make backups and update them as needed.
- Secure your browsing to stay safe against different types of malware.
Important -- edit the hosts file to unblock security websites
TL DR : The hosts file is edited to block security sites Before the virus can be removed, it's necessary to fix the hosts file (the file which controls which addresses connect to which IPs). That is the reason the majority of security websites is inaccessible when infected with this particular parasite. This infection edits this file to stop certain websites, including anti-malware download sites, from being accessed from the infected computer, making browsers return the "This site can't be reached" error. Luckily, it's trivial to fix the file and remove the edits that were made to it.Find and edit the hosts file
The hosts file can be found on C:/Windows/System32/Drivers/etc/hosts. If you don't see it, change the settings to see hidden files.- In the Start Menu, search for Control Panel.
- In the Control Panel, find Appearance and Personalization.
- Select Folder Options.
- Open the View tab.
- Open Advanced settings.
- Select "Show hidden files...".
- Select OK.
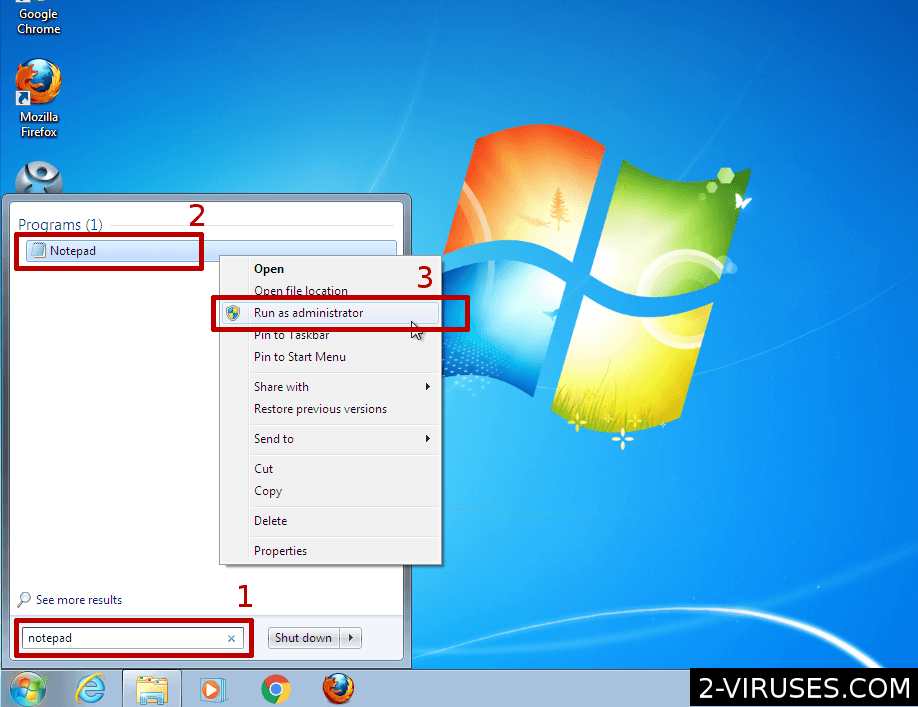
- Open the Start Menu and enter "notepad".
- When Notepad shows up in the result, right-click on it.
- In the menu, choose "Run as administrator"
- File->Open and browse for the hosts file.
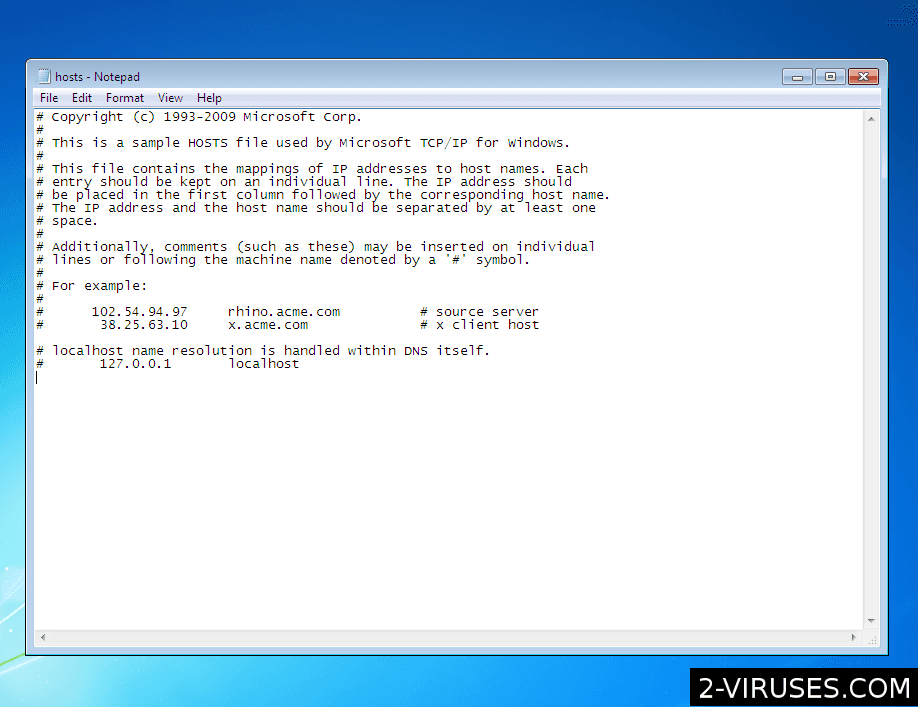 Delete additional lines that they connect various domain names to the wrong IP address. Save the file.
Delete additional lines that they connect various domain names to the wrong IP address. Save the file.
Download and run the antivirus program
After that, download antivirus programs and use them to remove the ransomware, the trojan, and other malware. Spyhunter (https://www.2-viruses.com/reviews/spyhunter/dwnld/).Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover Hets Ransomware encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before Hets Ransomware has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of Hets Ransomware
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to Hets Ransomware. You can check other tools here.Step 3. Restore Hets Ransomware affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually Hets Ransomware tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover Hets Ransomware encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.








