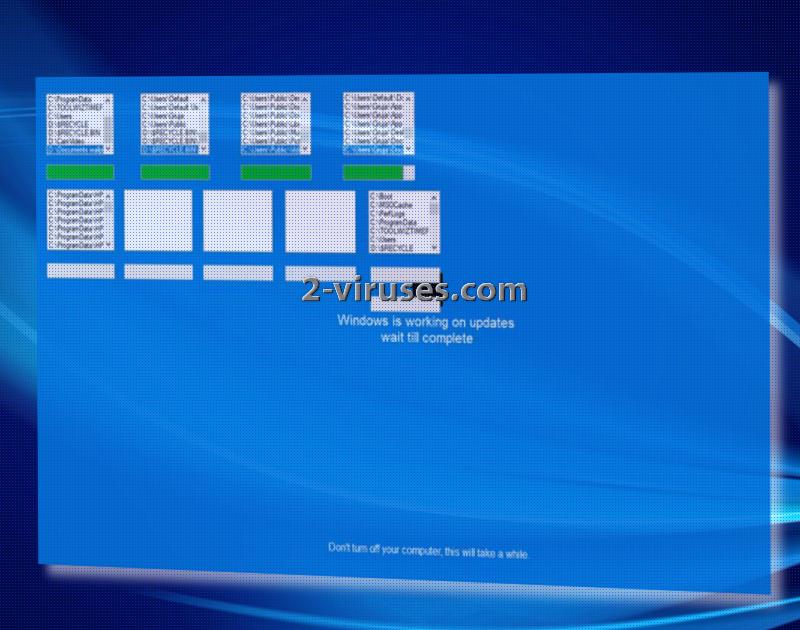
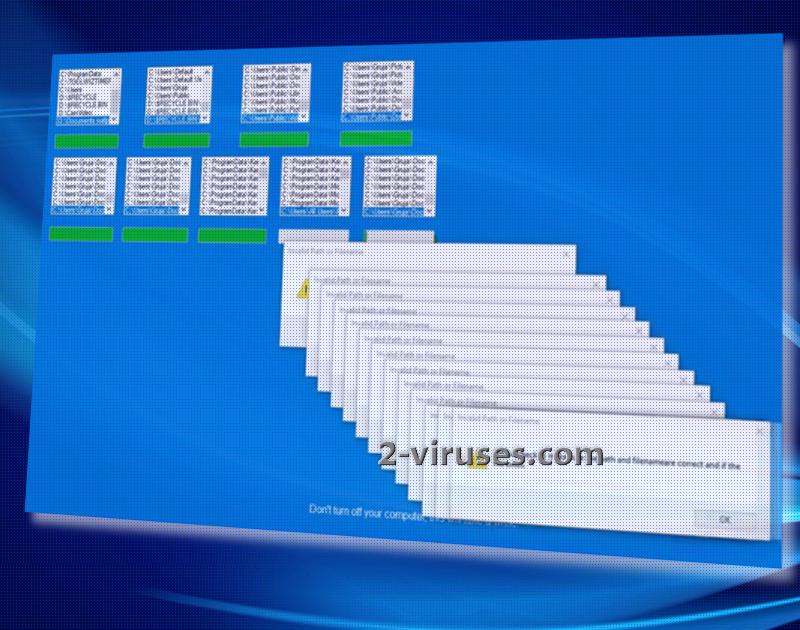
WhyCry ransomware virus endeavors to create a false impression: it feigns that users are installing an update for their Windows operating system. It features a blue screen which is to be accepted as a legitimate renewal from the Microsoft Corporation. The lock-screen instructs people to keep their devices open during the time that it appears to be scanning a variety of folders.
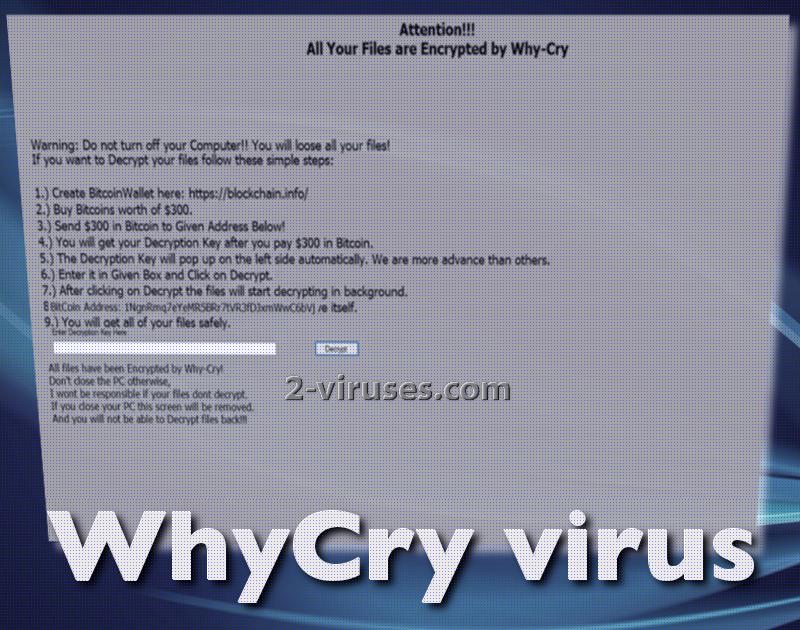
Once all sections are finished, the crypto-virus will reveal its true identity by showing the real ransom note. However, there is absolutely no need to pay the required fee for decryption, as this variant appears to be a newer version of Stupid ransomware infection. There is a decrypter you can use to recover all of your data.
Research about the infection
While user is under the false assumption that his/her operating system is being renewed, this is not the process that occurs behind the lock-screen. In reality, this is the time when the file-encryption is supposed to take place and turn all files completely worthless. After cryptography components have been applied to digital data, it will be inexecutable.
In this case, AES algorithm for encryption is applied and in the process of file-encoding, two keys are generated. In exchange for receiving the key for decryption, hackers are requiring victims to send 300 US dollars in the form of bitcoins, 0.11496 BTC. Do not act in haste and abide by the rules that hackers expect you to follow.
WhyCry-Ransomware.exe is revealed to be the malicious payload that initiates an activity of a ransomware. If you have never heard about the series of actions that are completed before the actual file-encoding, you should learn that these viruses have a specific way of proceeding. Firstly, the payload slithers into an operating system, then, it modifies Windows Registry Keys and scans hard drive for executables to ruin.
In the meantime, it does other operations as well, like reads active computer name or opens the Kernel security device driver (KsecDD) of Windows. Some variants contact hosts or send DNS requests, but this virus does not pursue this objective. .whycry extension is appended to the corrupted data and should help you figure out which data has been influenced by AES encryption. Considering the fact that Stupid Decrypter can help you restore data, you should not waste your money on a pointless cause.
You do not have to stand defenseless against ransomware: there is a number of ways to protect yourself from infections. One of the most popular and promising options is to store your files in backup storages or USB flash drives, whichever suits you better. This will help you to have spare copies of your files that will be waiting on standby for a moment to get you out of a complicated situation. If a ransomware infection ruins the copies that are found in your hard drive, knowing that your files are safe in an alternative location will calm you down.
In this case, if the fake lock-screen of Windows update appears, turn of your device before the encryption process is completed. Then, run your operating system once again and use an anti-malware program to detect the crypto-virus and to remove it. For this purpose, Spyhunter or Malwarebytes are perfectly-suited for the job. We always remind our visitors that files should be retrieved/restored only after the infection is exterminated for good. Security researchers have also published a video demonstration of the attack:
https://www.youtube.com/watch?v=GnLPJNyzLr4&t
There could be a number of methods that a ransomware virus can reach your operating system. A prevailing strategy is that payload can arrive via a deceptive email letter. If a source you do not recognize attempts to contact you, be careful with the content that it introduces you with. Attachments could easily be malicious and turn out to be malware.
Whycry Virus quicklinks
- Research about the infection
- Automatic Malware removal tools
- How to recover WhyCry virus encrypted files and remove the virus
- Step 1. Restore system into last known good state using system restore
- 1. Reboot your computer to Safe Mode with Command Prompt:
- 2.Restore System files and settings.
- Step 4. Use Data Recovery programs to recover WhyCry virus encrypted files
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,
How to recover WhyCry virus encrypted files and remove the virus
Step 1. Restore system into last known good state using system restore
1. Reboot your computer to Safe Mode with Command Prompt:
for Windows 7 / Vista/ XP
- Start → Shutdown → Restart → OK.
- Press F8 key repeatedly until Advanced Boot Options window appears.
- Choose Safe Mode with Command Prompt.

for Windows 8 / 10
- Press Power at Windows login screen. Then press and hold Shift key and click Restart.

- Choose Troubleshoot → Advanced Options → Startup Settings and click Restart.
- When it loads, select Enable Safe Mode with Command Prompt from the list of Startup Settings.

2.Restore System files and settings.
- When Command Prompt mode loads, enter cd restore and press Enter.
- Then enter rstrui.exe and press Enter again.

- Click “Next” in the windows that appeared.

- Select one of the Restore Points that are available before WhyCry virus has infiltrated to your system and then click “Next”.

- To start System restore click “Yes”.

Step 2. Complete removal of WhyCry virus
After restoring your system, it is recommended to scan your computer with an anti-malware program, like Spyhunter and remove all malicious files related to WhyCry virus. You can check other tools here.Step 3. Restore WhyCry virus affected files using Shadow Volume Copies
If you do not use System Restore option on your operating system, there is a chance to use shadow copy snapshots. They store copies of your files that point of time when the system restore snapshot was created. Usually WhyCry virus tries to delete all possible Shadow Volume Copies, so this methods may not work on all computers. However, it may fail to do so. Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8. There are two ways to retrieve your files via Shadow Volume Copy. You can do it using native Windows Previous Versions or via Shadow Explorer. a) Native Windows Previous Versions Right-click on an encrypted file and select Properties → Previous versions tab. Now you will see all available copies of that particular file and the time when it was stored in a Shadow Volume Copy. Choose the version of the file you want to retrieve and click Copy if you want to save it to some directory of your own, or Restore if you want to replace existing, encrypted file. If you want to see the content of file first, just click Open.
b) Shadow Explorer It is a program that can be found online for free. You can download either a full or a portable version of Shadow Explorer. Open the program. On the left top corner select the drive where the file you are looking for is a stored. You will see all folders on that drive. To retrieve a whole folder, right-click on it and select “Export”. Then choose where you want it to be stored.

Step 4. Use Data Recovery programs to recover WhyCry virus encrypted files
There are several data recovery programs that might recover encrypted files as well. This does not work in all cases but you can try this:- We suggest using another PC and connect the infected hard drive as slave. It is still possible to do this on infected PC though.
- Download a data recovery program.
- Install and scan for recently deleted files.