Detected in 2012 by Forcepoint (former Websense), Seculert and Kaspersky, Shamoon malware, aka Disttrack, has returned. On the 17th of November, 2016, at 20:45 local time Shamoon attacked a Saudi oil company Aramco. 30,000 computers have been affected. Shamoon, in the previous and in the recent attacks, has aimed at deleting the data from hard disks. Thus, it has been given the name of a disk-wiping malware. On an interesting note, in the attack of 2012 the wiped drives of the compromised computers were burned an image of a the flag of the Unites States set on fire, while in the current attack the famous photo, depicting the young Syrian refugee’s, namely, Alan Kurdy’s, body was used. The MBR (Master Boot Record) is overwritten so that the operating system of the computers would note be launched.
It is clear that before the actual attack has taken place, there had been some preparatory attacks carried out. These attacks involved the stealing of the passwords, which were later used in the main attack implemented by Shamoon. Unfortunately, there is not much known about the mechanism, which was utilized in these introductory attacks.
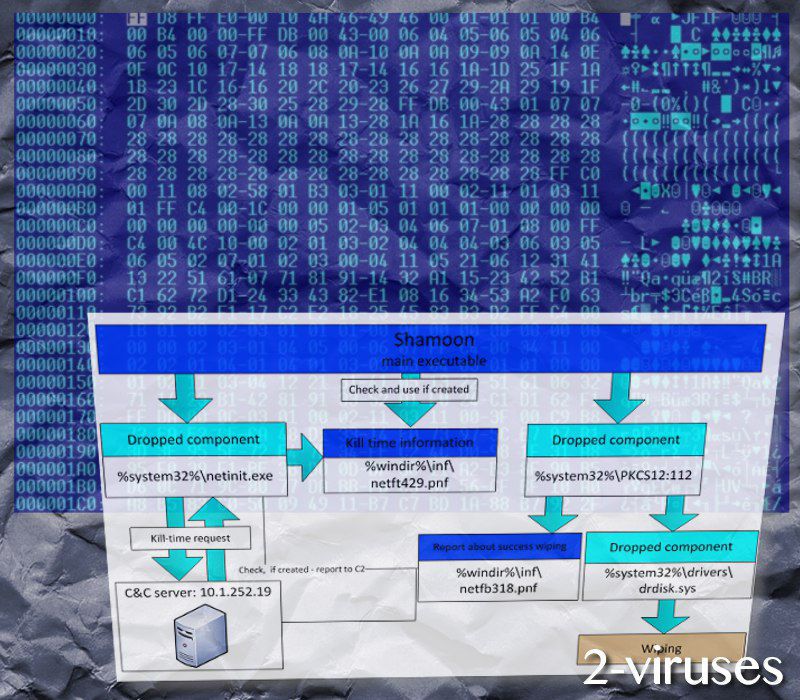
The Configuration of the Shamoon Malware
The composition of the Shamoon malware has not practically changed from that of the 2012 version. It is composed of three components: a dropper, a wiper and a reporter. The functions of the latter elements are the following. The dropper is responsible for the extraction of the supplementary segments and their execution. It is compatible with 32-bit, as well as 64-bit architectures and creates a service NtsSrv for its persistence on the system. It distributes itself among the computers of the network by self-duplication. The wiper is the actual hard disk wiper, enhanced by the RawDisk driver by EldoS, which enables Shamoon to directly access the hard disk, bypassing Windows OS. The wiper is the component, which deletes the data of the drives and copies the above mentioned image of the dead refugee boy on the drives of the infected computers. And, the reporter communicates with the C&C (Command and Control) server. These communications regard the downloading of extra binaries, changing the time of the attack, also the sending the confirmation message of the success of the attack.
On the Technicality of the Shamoon Malware
The executable file, that is, trksvr.exe locates itself at the %System% folder. This executable is associated with the dropper component. It spreads itself to ADMIN$, C$\WINDOWS, D$\WINDOWS, E$\WINDOWS network shares. The dropper also creates a task for self-execution and a service for being launched on the startup, namely, the TrkSrv service. It also drops the other two components onto the system.
While the wiper is associated with [NAME SELECTED FROM LIST].exe. The list is the following:
caclsrv, certutl, clean, ctrl, dfrag, dnslookup, dvdquery, event, extract, findfile, fsutl, gpget, iissrv, ipsecure, msinit, ntx, ntdsutl, ntfrsutil, ntnw, power, rdsadmin, regsys, routeman, rrasrv, sacses, sfmsc, sigver, smbinit, wcscript
Thus, it can be any name of the list that the wiper could be called. The wiper performs the execution of the following commands to accumulate the name of the files to be overwritten:

The files selected, then, are overwritten with the JPEG image specified earlier in the post. After their successful rewrite, they become unreadable. In the end, the MBR is overwritten and the computer cannot be loaded:
Interestingly, the following pop-up warning is displayed before the shutting down of the system:
The component of the reporter, placed in the same directory, comes under the name of netinit.exe. The reporter communicates with the C&C via a HTTP GET request, which has the following structure:
http://[DOMAIN]/ajax_modal/modal/data.asp?mydata=[MYDATA]&uid=[UID]&state=[STATE]
Through HTTP POST request the reporter sends the following data: the name of the domain, the number of the overwritten files, the IP address of the computer, and a random generated number.
Spyhunter and Malwarebytes can detect Shamoon malware.
Automatic Malware removal tools
(Win)
Note: Spyhunter trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions,
(Mac)
Note: Combo Cleaner trial provides detection of parasites and assists in their removal for free. limited trial available, Terms of use, Privacy Policy, Uninstall Instructions, Refund Policy ,